Does this sound familiar? Your organisation has invested heavily in Microsoft 365 security. You’ve enabled Microsoft Defender. You’ve configured Conditional Access policies. You’ve rolled out sensitivity labels and Data Loss Prevention (DLP). Multi-factor authentication is mandatory.
So, why doesn’t your environment feel more secure?
The answer might surprise you: security tools don’t actually create security. They enable it, people and processes are what make security real.
We work across industries like banking, government, healthcare and construction, where protecting information is critical. And time after time, we see the same thing, teams focus on deploying tools instead of strengthening the foundations that make those tools effective.
In this blog we unpack why that happens, and what actually makes Microsoft 365 environments secure.
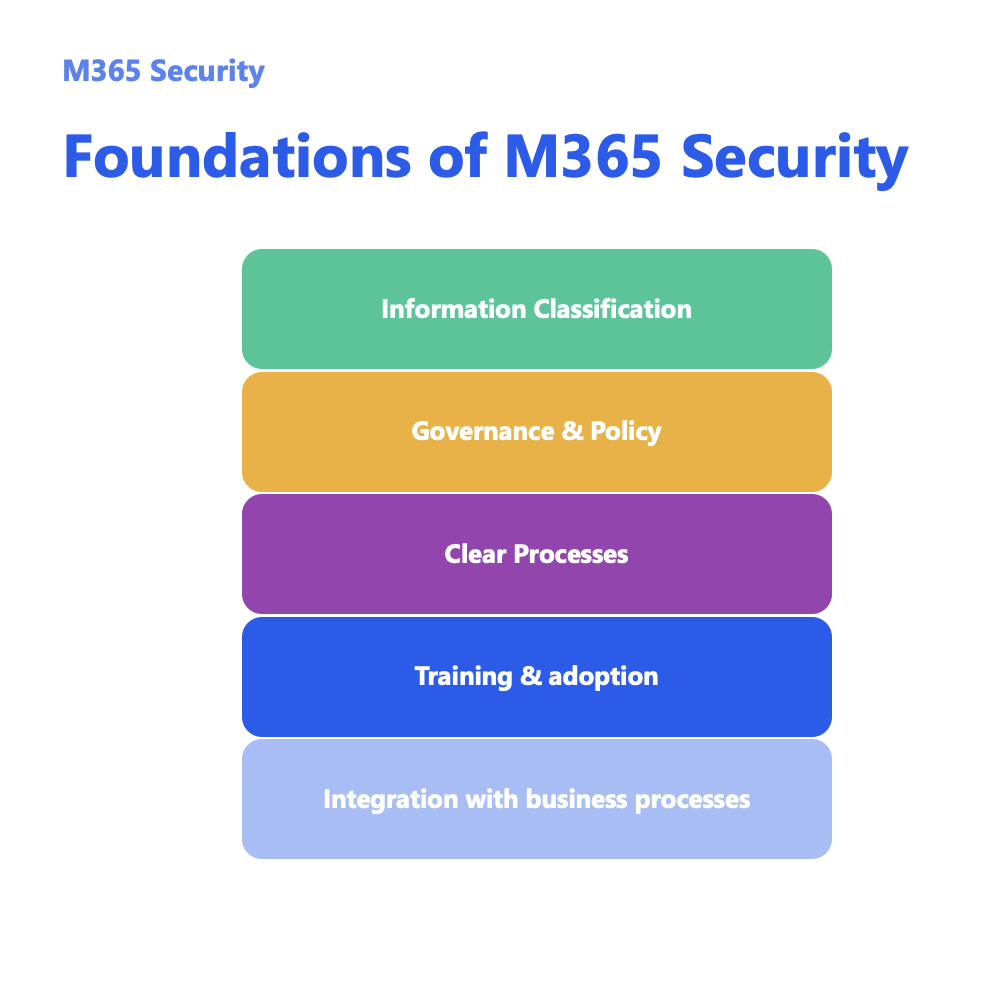
The tool-first trap, and why Microsoft 365 security tools aren’t enough
Here’s a common scenario.
A data breach hits a competitor. Executives panic and IT is told to “lock down” Microsoft 365. The team moves fast by enabling new features, tightening access, and turning on every alert possible.
Six months later, the environment looks more secure, and technically has more controls, but everyday work has become harder:
- DLP policies are blocking legitimate work because there’s no clear classification framework defining what needs to be protected
- Sensitivity labels sit unused because employees don’t understand what “Confidential” means or when to apply it
- Security alerts pile up unaddressed because there’s no process for triaging and responding to them
- Conditional Access policies are inconsistently applied because there’s no governance framework defining risk levels and access requirements
- External sharing is still happening inappropriately – people just find new workarounds because the policies don’t match how work actually gets done
The tools are running and the dashboards show “protected” status. But, is the organisation actually more secure? Spoiler alert: Not really! Because without foundations, tools are just… tools.
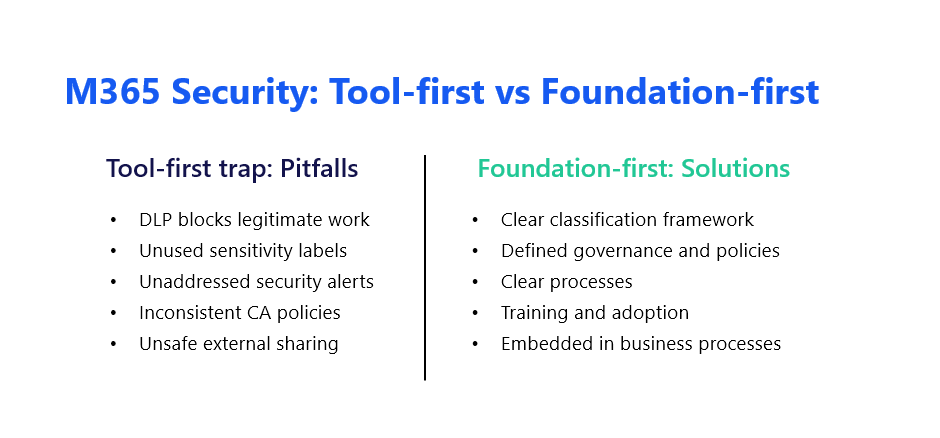
What’s missing? The five foundations of real Microsoft 365 Security
The tools are important, but they only work when the right foundations are in place. Real security starts with how your organisation thinks about, manages and responds to risk, not just with what’s been turned on in the admin centre. Here are five foundations to put in place that make the biggest difference.
1. Information Classification Frameworks
Before you can protect data, you need to define what needs protecting and why. What’s the difference between “Internal” and “Confidential”? Who determines classification? How does classification relate to access controls?
DLP policies are only as good as the classification scheme they enforce. Without a clear, business-aligned framework, DLP becomes guesswork – either too restrictive (blocking legitimate work) or too permissive (failing to protect what matters).
2. Governance and Policies
Security tools automate enforcement, but they need something to enforce. Who can share externally? What data can leave the organisation? What apps are approved for business use? How do we handle guest access?
These aren’t technical questions – they’re business decisions that need governance frameworks. Tools like Conditional Access and external sharing controls can’t make these decisions for you; they can only enforce decisions you’ve already made.
3. Clear processes
When Defender flags a suspicious email, who investigates? When someone requests access to sensitive data, who approves? When a DLP policy blocks a document, how do users escalate?
Security tools generate events and alerts. Without processes to handle them, they just create noise. Without a process, the most sophisticated monitoring in the world is worthless because no one knows what to do with the alerts.
4. Training and adoption
The uncomfortable truth is that the most common security failure isn’t technical, it’s human. It often comes down to people. Users click phishing links, misclassify documents, share inappropriately, or work around controls that seem unnecessarily restrictive.
This isn’t because users are careless. It’s because they haven’t been brought along on the security journey. They don’t understand why security matters, what they’re protecting, or how to work securely. They see security as an obstacle to their work, not an enabler of it.
5. Integration with business processes
The most effective security is embedded into business processes, because security works best when it’s built into the way people already work, not bolted on afterward. When people can collaborate securely without friction, they will. When security creates unnecessary obstacles, they’ll find workarounds – and those workarounds are usually less secure than doing nothing.
An example of Microsoft 365 security that works
Let’s look at a different scenario:
An organisation is preparing to deploy Microsoft 365 Copilot. Before turning it on, they take a different approach by ensuring governance and management first:
- They take the time to assess their information landscape to understand what data exists, where it’s stored, and who has access
- They build a classification framework aligned to their business needs and compliance requirements
- They implement governance policies defining who can share what, with whom, and under what circumstances
- They train their people on information security – not just “don’t click links” but genuine understanding of data protection
- They configure the tools (sensitivity labels, DLP, external sharing controls) to enforce the frameworks and policies they’ve created
- They establish processes for handling exceptions, escalations, and and incidents
Now when they deploy Copilot, the security tools work. DLP doesn’t block legitimate work because the classification is clear. Labels get applied because people understand them, and alerts get handled because there are processes in place.
What you can see here is the tools are the same as above, but the outcome is completely different. The key difference? In this scenario they built their foundation before they applied the tools over the top.

Why strong security matters more than ever
Microsoft 365 is evolving rapidly. Copilot, and generative AI as a whole, is fundamentally changing how people work with information within the Microsoft 365 ecosystem. Regulatory requirements are tightening.
As we mentioned, organisations that built their M365 security on tools alone are discovering that foundation is shaky. As capabilities expand and risks evolve, the gaps become more apparent and more dangerous.
The good news is, it’s never too late to build the foundation, it just requires a shift in thinking.
So, we end this blog with some parting words of wisdom:
Stop asking “what security tools should we deploy?”
and instead, start with “what security outcomes do we need, and what foundations will deliver them?”
Like what you see?
At Engage Squared, we help organisations build the foundations that make Microsoft 365 security work, from information governance and classification frameworks to policies, to adoption programs and strategic assessments.
We’re also proud to have been recognised by Microsoft as a Solutions Partner for Security, an acknowledgement of our proven expertise in helping organisations protect their people, data and systems.
If you’re looking to strengthen your security posture or just want to know where to start, get in touch with our team today.
About the author
Andrew Nathan is a Principal Information Security Consultant at Engage Squared. He helps organisations turn Microsoft 365 security tools into real security outcomes through practical governance, data protection, and user-centric adoption.
Before joining Engage Squared, Andrew led Security for Microsoft FastTrack for Azure in the Americas and served eight years in the Australian Army, including time in Special Forces. He holds a Master of Business Administration and a Bachelor of Science in Information Technology and is a Certified Information Systems Security Professional (CISSP).